The Internet and technology, combined, have become primary aspects of our daily lives. As our reliance and dependency grow on them, the risk of cyber threats increases. Hence, to tackle them, automated penetration testing tools are acting as a rescue force. Over time, automated testing significantly started replacing manual testing due to its ability to work faster, smarter, and produce accurate reports. Therefore, with the introduction of AI and ML, the importance of penetration testing tools is soaring.
As a result, businesses today, including online shopping and crypto markets, are already using these tools as their foremost security mechanism. So, moving forward, keep reading our blog to gain a detailed overview of these automated tools.
What are automated penetration testing tools?
Automated penetration testing tools are the ones that simulate cyberattacks on the network or software system, just like hackers, to uncover the vulnerabilities. As a result, these tools are designed to identify a wide range of security loopholes and provide continuous protection against cyber threats.
Sectors like web applications, mobile applications, network infrastructure, cloud, and social engineering mainly use these testing tools. It is believed that the automated penetration testing service market size will evidently grow to an estimated value of 2.7 billion by 2027 globally, with steady growth of 13.7% as per CAGR.
Many countries, including India, China, and Japan, are also widely adopting automated penetration testing technologies with strict compliance guidelines to protect their data. Regardless of scale, these tools provide high security without affecting the work efficiency of organizations. In short, automated penetration testing tools are a necessary add-on for businesses.
How significant are the automated penetration testing tools?
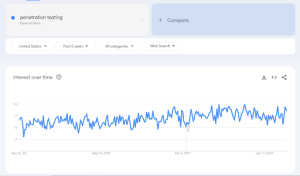
As per the latest Google Trends reports, there has been an observable gradual growth in “penetration testing” for the last few years. Therefore, given this rise in web search, there is a projected increase in the rate of penetration tools as well.
As a result, this can be predominantly reduced by choosing automated penetration testing tools instead. It has benefits like:
Improves productivity
Opting for automation testing tools helps testers decrease their stress and work on multiple projects. As a result, right after the penetration test is complete, testers have an accurate report of casualties, which assists them in improving the software productivity.
Block cyberattacks
Automated penetration testing software helps to understand the team’s capability to respond and control the cyber-attacks. Thus, after thoroughly assessing the weaknesses, a detailed report on improving factors helps the team upgrade their security.
Reliability
Many CRM businesses thrive on securing customer data to go a long way in business. For them, reliability is the key to keeping their services on deck. Hence, integrating the services with the automated penetration software tools leads them to the best security front.
How is automated penetration testing conducted?
Certainly, a penetration tester is responsible for not only building a security mechanism for the system but also estimating the level of damage it can prevent. Hence, the tester includes using automated penetration testing tools for accurate processes within stages:
Planning stage
Identifying the systems to test, in addition to estimating the flaws in the network, is the main goal of the planning stage. A complete diagnosis will help to set the target within the necessary domain to be used to unearth the vulnerabilities in the systems.
Scanning stage
Using black box or white box testing can help to unravel the possibilities of cyber attacks. Hence, employing a static or dynamic code analysis can be of good use. Also, monitoring the real-time application performance can help increase the level of network performance.
The control and breach stage
After scanning, the next stage is to gain access and target acquisition. We can use cross-site scripting or backdoor techniques to estimate the potential security breaches. Additionally, we can exercise control to exploit the vulnerabilities while intercepting traffic.
Reporting stage
The automated penetration testing tools, in this stage, help the tester to control the security breach and give a detailed report about contemplating loopholes. As a result, on successful initiation of the software, the data becomes completely secured.
What are the popular automated penetration testing tools?
By now, readers would be familiar with the automated penetration testing service and its benefits. As a result, in this section, we will talk about both commercial and open-sourced popular testing tools that are used globally. They are:
Metasploit
Metasploit tops the list inarguably because of its best penetration testing services, both manually and automated. It has a group of tools to verify and withstand various cyber-attacks. Besides, its functionalities are adaptive and customizable as well.
Burp Suite
Burp Suite is an integrated platform for performing thorough security tests on web applications from initial mapping to the application attack surface. As a result, it is one of the most influential tools to find security vulnerabilities in the software system.
Acunetix
This tool is a completely automated web security tool. It’s capable of inspecting different web applications for vulnerabilities. As a result, it generates accurate test reports. Also, CMS systems, HTML, and one-page applications all can opt for this.
Nikto
Nikto is an open-source penetration testing software that identifies nearly 6000-7000 malicious files and performs generic checks to spot outdated server software. Similar to its nature, it also follows strict disruptive legal and ethical guidelines.
Wireshark
Wireshark analyzes network traffic, troubleshoots issues in the network, identifies potential security threats, and performs penetration testing for home office or internet connection. Due to its vast range of features, it is also called a packet sniffer in the world.
Nmap
Nmap is also one of the open-source penetration testing tools. In addition to a vulnerability scanner, it also works for cloud network management and monitoring. Moreover, it quickly identifies the critical boundaries in the network and helps the tester to improve them.
How to choose the right automated penetration testing tools?
With a single decision of choosing the right automated penetration testing tools, you can change your gameplay against peer businesses. Did you know? Stack Watch 2021 Vulnerability Report stated there were 20,174 security vulnerabilities (CVEs) published in 2021 compared to the previous year, which had bordered around 17,049. As a result, here are some of the crucial steps that you need to be mindful of:
Based on the test needs
Prepare a checklist for necessary tests to be performed on software systems. As a result, it will help you understand what type of platform to choose from. For example, a school portal or a normal website would require less security compared to government-related portals.
Within budget
Automated tools aren’t necessarily costly, but depending on our requirements, the costs may differ. If you require more functionalities, the costs may also rise up. Hence, before selecting the automated penetration tool, always plan according to your budget, as there are other related expenses, too.
System compatibility
To integrate the automated penetration testing tool with your existing system. It’s necessary to check whether the tool is equally supportive and compatible with the existing framework. As a result, always check which should be efficient in improving overall security.
Accurate reports
Make sure the penetration testing tools you choose are well-equipped to identify possible vulnerabilities. The tools must be able to identify errors and produce correct reports. Additionally, they must provide security solutions to the testers to fill all the possible loopholes.
Compliance standards
Last but not least, it is crucial to verify if testing tools adhere to significant regulatory and compliance standards, such as GDPR, ISO 27001, and PCI-DSS, before generating any specialized compliance report. These standards, as a result, aid companies in avoiding penalties in the future.
Conclusion
Data being completely computerized, from large businesses to commoners, everyone is prone to cybercrimes. Devices using public LAN connections and shared wireless connections are easy targets for hackers. Using a strong security front for data protection is our responsibility. By now, readers would have an idea about how opting for automated penetration testing tools and methods can make you a game-changer and least vulnerable even before any attack.
Build your defense with automated penetration testing tools and claim victory against every cyberattack!